A new Subgraph OS Alpha ISO is available for download.
This is a release mainly targeting some bugs that were present in the last available ISO.
We are working on some major new features that aren't done yet or aren't yet robust enough to be included in a release to users. Some of those new features are described below.
We really should have released an ISO sooner than this as there were some annoying bugs that got in the way of new users trying Subgraph OS for the first time. We've setup a new, more aggressive release schedule and should be making non-release ISO builds available as we produce them monthly.
New features: Alpha release 4
Ther are some new features in this ISO. Note that existing users should have most of these, as Subgraph is a rolling release distro.
One exception is the HexChat default configuration for use with SOCKS5, implemented with a default config put in /etc/skel/.config/hexchat.
1. Multi-bridge (including clearnet) support in Oz
Oz now has support for an arbitrary number of named bridges to be created and attached to sandboxes to support flexible layer 3 network exits. We have included chromium as the first default configuration that uses this feature to provide a clearnet browser. To get the chromium clearnet browser, just run:
sudo apt-get install chromium
..and chromium should be setup as the clearnet browser in Subgraph OS. We will likely include chromium in the next ISO.
There is also a proof-of-concept implementation for launching OpenVPN and wiring a sandbox bridge to the tun device. Try it, but don't rely on it: it's fragile and insecure, and we know that. We intend to make substantial improvements to this for future releases, as well as support other VPN technologies.
2. Use of GPG restricted socket in Thunderbird sandbox
We redesigned the Thunderbird sandbox so that private keys are not accessible in the sandbox, and decryption/signing operations are requested via gpg-agent through the GPG restricted socket.
3. Experimental support for launching ephemeral sandboxes
There is an experimental feature that allows for users to optionally launch sandboxes without any persistence. To enable this, add the following to /etc/oz/oz.conf:
, "enable_ephemerals": true
Following this, launching sandboxes will produce a pop-up asking if the sandbox should be launched ephemerally. We will make this less annoying in the future as this feature becomes more robust.
4. Rework of XDG_DIRS in sandbox filesystem
In earlier versions of Subgraph OS, users would have to remember to use a a special shared folder in a sandbox that applications would have no awareness of. We've automatically mapped the XDG_DIRS directories to shared folders outside of the sandbox, which improves the user experience within applcations. For example, Chromium downloads will be saved to a location accessible outside of the sandbox without any extra user interaction.
The only exception to this is Tor Browser, which still saves downloads to .local/share/torbrowser/tbb/x86_64/tor-browser_en-US/Browser/Downloads/, which we acknowledge is ridiculous and will be addressing as soon as possible.
Improvements and bug fixes
- Pure UEFI boot fixed
- Hexchat default configuration is to use a SOCKS5 proxy
Known issues
Subgraph OS is a work in progress, and major changes are underway. There are some important issues users should be aware of. Some of them are included below; for more, review the open issues at our Github repository.
1. System time at startup in live mode and after first install
Requiring system time be already set to the correct time is still an issue for bootstrapping Tor. We will address this issue in the coming ISO.
2. Tor Browser writeable in home directory/sandbox
Tor Browser Launcher installs Tor Browser into the user's home directory, where it ends up being writeable in the sandbox. This is a long-standing issue we hope to address soon.
3. OpenVPN client runs as root
Our implementation of support for OpenVPN is very rudimentary and experimental. There are a number of options on the table for us to support it in a way that's much more safe and robust, and implementing this is a work in progress. Part of the reason we are taking our time is because we want to support multiple modes: attaching the tun device to a bridge that is used by multiple sandboxes, for example (this is not yet possible). We can also put a tun device into the namespace of a single sandbox and remove all exposure of the host routing table to the VPN server.
Coming soon
Here's a preview of some of the things we're working on and are excited about.
1. Major Subgraph Firewall improvements
We're working on some major improvements to Subgraph Firewall. These include:
- A SOCKS5 application firewall (i.e. filter Tor access)
- TLSGuard
- UDP and ICMP support
- Sandbox awareness and policy support
If we can fix all bugs and are happy with the user interface changes, we'll release this in the next ISO.
Screenshot:

2. Support for terminal applications in Oz
Oz will support terminal applications with seccomp-bpf whitelists installed. We also sandbox gnome-terminal.
3. System-wide Tor through Subgraph Firewall
With support for a SOCKS5 filter, we'll be able to apply system-wide filtering of network exits via Tor. No unprivileged process will have direct access to the Tor SOCKS5 port: they will have to go through Subgraph Firewall, where mandatory TLS can be enforced on a per-process/application basis. We are currently testing this and working out bugs.
4. Support for USB devices in sandboxes
We've been working on dynamic support for popular devices such as Yubikeys and hardware cryptocurrency wallets. This has been prototyped and we have had Yubikeys working with Chromium in an Oz sandbox, as well as Ledger Nano S in an Electrum sandbox.
5. i2p Support
We have successfully implemented experimental support for i2p, with specific sandboxes (HexChat, Chromium) configured to exit via i2p tunnels (see note below on Chronion re: privacy issues with Chromium).
6. "Chronion", a sandbox profile for using Chromium with Tor
Chronion is an experimental sandbox configuration for the Chromium that launches it so that it exits via Tor. The Chronion profile also enforces ephemerality so that there's no persistent state left (apart from an optional shared Downloads/ folder) between instantiations. The Oz sandbox runtime also prevents known leaks of interface IP addresses via webrtc.
The primary reasons for a Chromium-over-Tor sandbox configuration are superior security against browser exploits and performance.
There are privacy drawbacks to using Chromium with Tor, and we have been reluctant to make this widely available for those reasons. At a minimum, Chromium is likely less resistant to known browser fingerprinting attacks mitigated by Tor Browser's pro-privacy and anti-fingerprinting customizations. We will elaborate on this in a future blog post.
Screenshot:

7. Support for WireGuard and other IPSec based VPNs in Oz
We have successfully setup Oz sandboxes that exit via wg interfaces, and there should be no reason why we cannot also support any IPSec based firewall. This is a work in progress being implemented alongside the very basic and experimental support for OpenVPN.
8. Better support for Tor configuration, bridges
We're improving support for configuration of Tor, both in live mode and for installed users. This includes managing bridges via a GUI, and providing more control over how/when Tor bootstraps.
9. Non-Tor mode
Subgraph OS without a default system-wide Tor exit is planned for the future, with use of Tor and other alternate network transits manageable on a flexible, per app/sandbox basis (or system-wide perhaps if chosen during install).
Follow us on Twitter at @subgraph as well as at this blog for progress updates.
A new Subgraph OS Alpha ISO is available for download.
New features: Alpha release 3
1. ROFLCoptor Tor Control Port Filter and State Tracker Daemon
ROFLCoptor filters Tor control port traffic. It is configured with application-specific security policies to limit what actions may be performed through the control port. ROFLCoptor also includes integration with OZ for dynamic port forwarding capabilities to support fully sandboxed applications that create ephemeral Tor hidden services, such as OnionShare, Ricochet, and Bitcoin core.
2. OnionShare
Subgraph OS now includes OnionShare. OnionShare is an application for sharing files securely and anonymously over the Tor network. OnionShare is fully sandboxed in OZ and has been integrated into the Nautilus file manager (right-click on file to share over OnionShare).
3. Ricochet
Ricochet is an anonymous peer-to-peer instant messager. It is different from other instant messagers because instead of using central chat servers, users connect directly to one another over Tor hidden services. Ricochet runs fully sandboxed in OZ.
4. Subgraph OS Handbook
We have included our documentation in the operating system. A shortened version can be read from the desktop (using yelp). The complete documentation (HTML, PDF) can be found in the following directory: /usr/share/sgos-handbook/
Improvements and bug fixes
Our last ISO was released in June. There have been many improvements and fixes since. We'd like to highlight a few major ones.
1. Our Grsecurity kernel has been upgraded to version 4.8.15
Among other improvements, this fixes the "Dirty COW" vulnerability (CVE-2016-5195). We addressed this vulnerability earlier for users who have installed Subgraph OS. It is now addressed in the live disc as well.
2. MAC address spoofing has been fixed
For as long as memory serves, Linux users have used if-pre-up scripts to accomplish
MAC spoofing for network interfaces. A number of years ago changes in NetworkManager
broke this functionality. This bug first reported in 2010
remained unfixed until a couple of years ago, however the implemented fix via nm-dispatcher did not actually
allow for MAC Spoofing and was only helpful for bringing up iptable rules.
Thankfully a reliable method was implemented via udev to spoof on boot. Recently, NetworkManager started implementing some new MAC spoofing technics of its own. However these are not yet fully capable, and broke the udev technique in passing. Thankfully upstream quickly provided a fix this time around. This means that our udev based mechanism works again. This required a configuration change for NetworkManager to "preserve" spoofed MAC addresses.
3. Audio issues addressed in OZ
We have updated the PulseAudio configuration to correct audio-related issues in sandboxed applications.
4. Application firewall improvements
The application firewall now includes "system" rules. These are the default rules for Subgraph OS. With this upgrade, they are now treated differently than the user-defined rules. The firewall settings UI has been updated to reflect this change. We have also improved the usability of the firewall settings UI and Prompt.
5. OZ now includes support for dynamic forwarders
Dynamic forwarders lay the groundwork for running servers in the OZ sandbox. This has enabled us to support OnionShare, Ricochat, and Bitcoin core, which all both start Tor hidden server servers in the sandbox. Incoming client connections are forwarded into the sandbox.
6. This release addresses the APT signature verification vulnerability
(CVE-2016-1252)
CVE-2016-1252 is now addressed in the live disc. Subgraph OS is only distributed for the x64 architecture, so it was not believed to be at risk. This release closes the vulnerability completely.
7. Port to gosecco
In this release we have integrated a new Go seccomp-bpf library developed by the ThoughtWorks Tiger team. Gosecco allows us to create more expressive and efficient policies for our sandboxed applications.
Acknowledgements
We would like to thank everybody for all of your help and feedback during the Alpha. We expect to have a Beta out sometime in 2017. There are some people we'd like to call out specifically:
Stephen Watt (@uT_infection) for a bunch of stuff, notably assisting greatly with porting the seccomp-bpf policy generator to gosecco as well as the early version of the log monitor
Leif Ryge (@wiretapped), Claudio Guarnieri (@botherder), Will Scott (@willscott), Special (@jbrooks_), Donncha O'Cearbhaill @DonnchaC, and Rafael Bonifaz (@rbonifaz) for testing and valuable feedback
@david415 for contributing ROFLCoptor + some help from @wiretapped
Alison Macrina (@flexlibris) for numerous bug reports and help testing
@femmetasm for testing, patient help bugfixing, and useful ideas
ThoughtWorks Tiger/Strike teams: Ola Bini (@olabini), Yakira Dixon (@ultrastoic), Rosalie Tolentino (@rosatolen), Chelsea Komlo (@chelseakomlo), Fan (@tcz001), Tania Silva (@tdruiva), Reinaldo Junior (@reinaldojunior), Ivan Pazmino (@iapazmino) for: CoyIM, gosecco
Follow us on Twitter at @subgraph as well as at this blog for progress updates.
We are happy to announce that Subgraph is to receive support for 12 months of Subgraph OS development from the Open Technology Fund.
This means that we will be able to focus our efforts over the next year on development exclusively.
Our current areas of focus are:
Oz, our framework for application isolation
Tooling and automation for builds and tests of Subgraph OS packages as well as for the base OS image. We are working towards a downloadable ISO as soon as possible.
All of our code is to be hosted on Github, though for now everything there is very alpha. We invite the community to check it out.
Follow us on Twitter at @subgraph as well as at this blog for progress updates.
We will be posting soon about Oz.
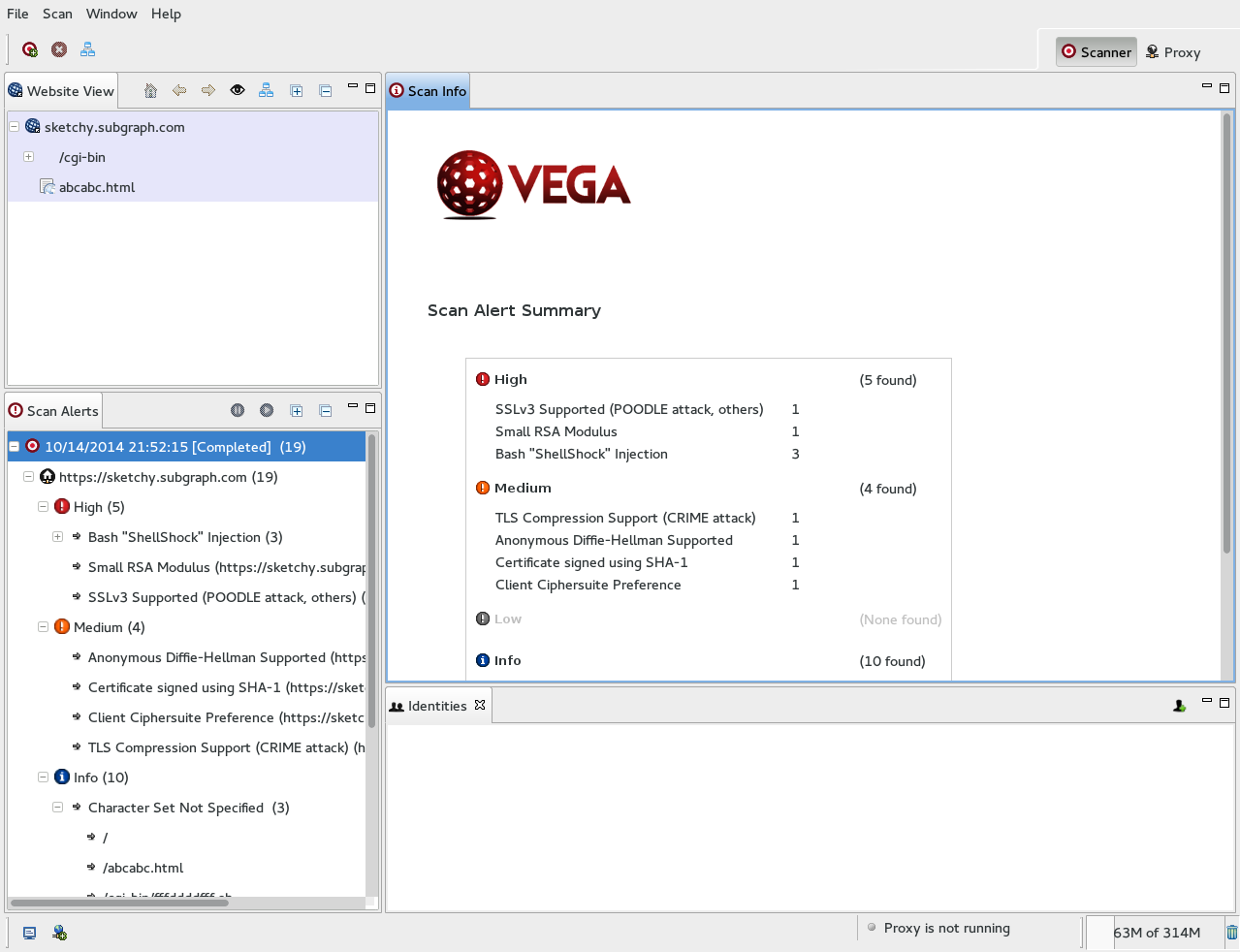
We recently added a feature in Vega: probing HTTPS server configuration settings for issues that have implications for user and application security.
Vega now attempts to detect and will alert on the following issues:
- SSLv2, SSLv3 (POODLE) support
- Certificate analysis: SHA-1, MD5, key size
- Server/client ciphersuite preference
- Forward secrecy support and prioritization
- RC4
- Cipher suite enumeration
- Identifcation of weak / export grade cipher suites, anonymous Diffie-Hellman
- TLS compression (susceptibility to CRIME attacks)
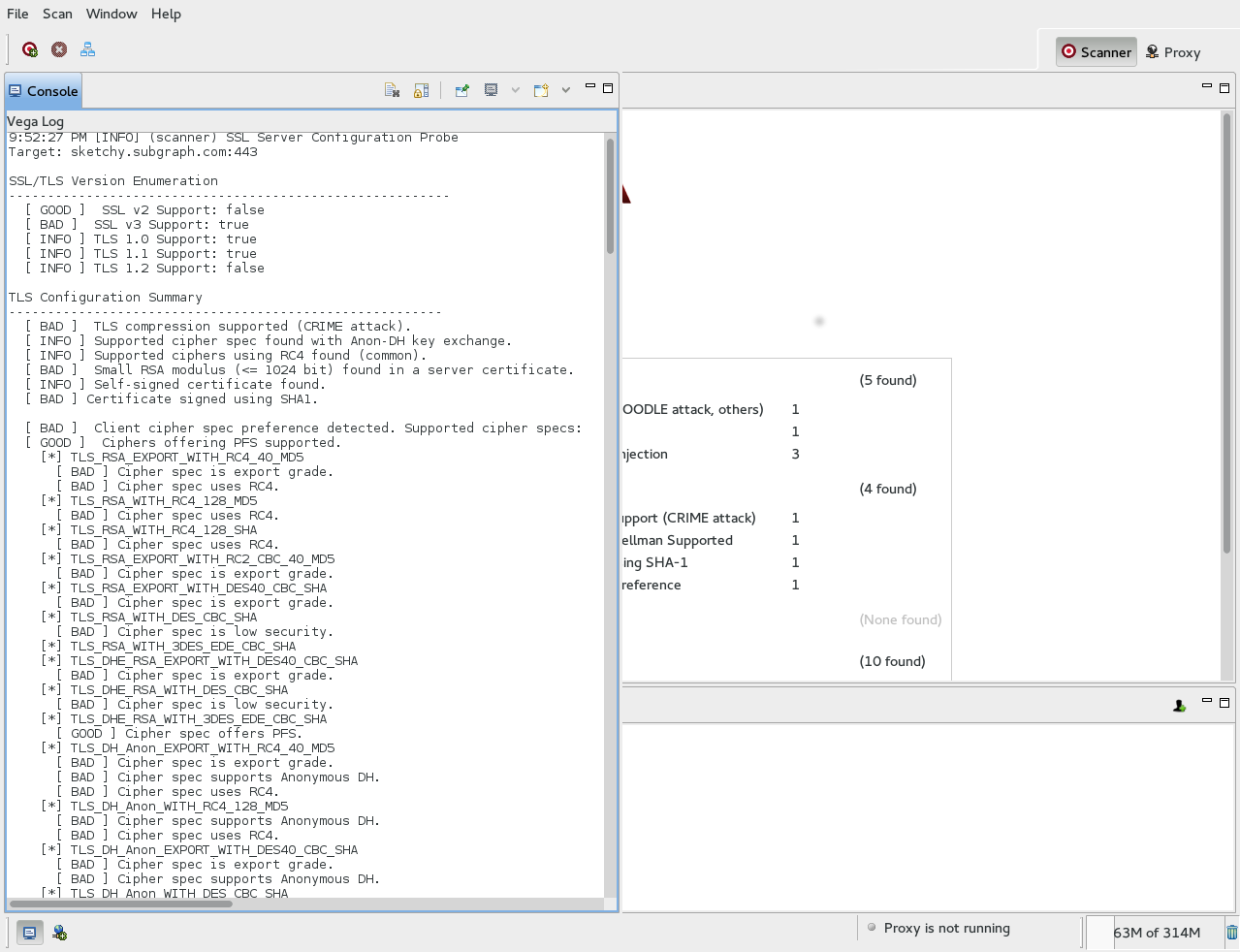
The probes occur before the crawler is started and will run for every HTTPS server target. Full details on the HTTPS audit will be output to the console after the probes have finished running.
This is still a work in progress, so consider it a beta release. The Vega HTTPS server configuration probing will be more comprehensive, reliable, and configurable in the future.
Download a new build from our website to try it out.
We put up a new Vega build (118) that includes an improved Shellshock module and fixes a couple of bugs.
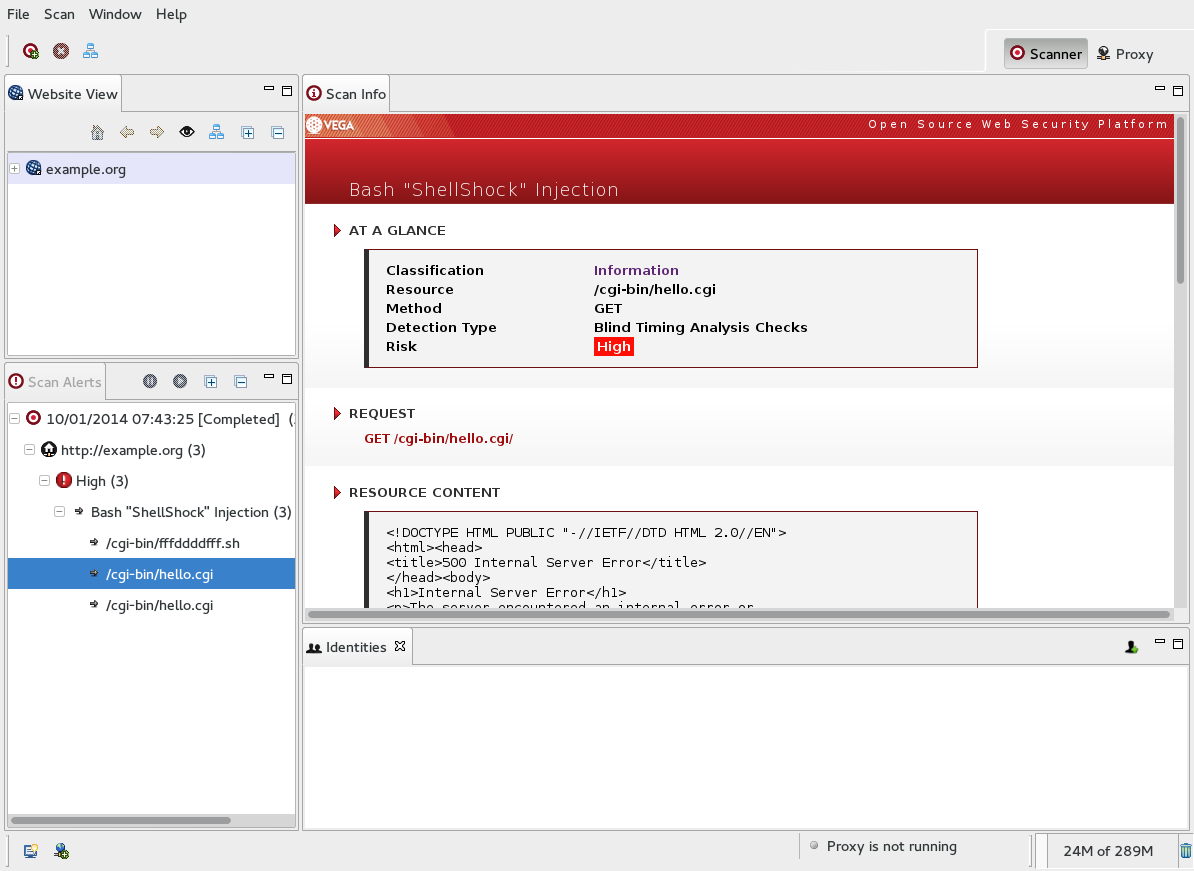
Today, a critical and trivially remotely exploitable vulnerability was announced in bash. To help users of our Vega web application scanner to identify this vulnerability, we have a released a basic standalone module to detect this vulnerability in web applications.
The module works by injecting test cases into certain HTTP header values as well as any web application form/query parameters. This should be adequate to detect this vulnerability in CGI setups where HTTP header values are turned into bash environment variables while also detecting cases where user-supplied input is passed through functions that spawn subshells such as system(), exec(), popen() in various languages. We will refine the module as more information becomes available and we are able to test it more.
This module is a good example of the power of Vega to quickly create proofs-of-concept in Javascript using the module API.
The module can be obtained here. It can be installed simply by adding it to the ‘vega/scripts/scanner/modules/injection/’ directory.
If you are not a Vega user, you can download it here or build it from source. We will soon bundle this module into our release tarball.
Due to the seriousness of this vulnerability, we also strongly advise everybody to install patches immediately.
Geary is a nice looking mail client for Linux / Gnome users.
We identified a vulnerability in Geary during some recent testing related to Subgraph OS, Mail and Nyms. Thankfully the maintainer responded to our report really quickly and there has already been a patch committed and backported. There are updated tarballs on the Geary homepage and hopefully distro upgrades will be available soon.
Here are the details on CVE-2014-5444:
When Geary connects to any server endpoint over SSL/TLS (IMAPS, SMTPS, IMAP + STARTTLS, SMTP + STARTTLS), it doesn’t act on certificate validation errors, which are detected but ignored. Further, the user is not even made aware when certificate validation fails except when Geary is run with optional debug output via the -d command-line switch.
In all validation failure cases the user credentials are transmitted to the server. This creates an effective attack to harvest user email passwords through active interception.
Geary is fairly identifiable on the wire, meaning that an adversary in a position to perform the attack can do so selectively, reducing the likelihood of detection if another, non-vulnerable mail client is intercepted.
One way to fingerprint Geary is to observe the IMAP IDLE refresh frequency, which occurs every 30 seconds. This is unusually short compared to the maximum IDLE limit of 30 minutes and the default behavior of other clients (Evolution: 10 minutes, Thunderbird: 10 minutes, Claws Mail: 5 minutes).
If exploited, an interception attack would not be perceptible to most users.
Here’s the problematic code, take note of the TODO in engine/api/geary-endpoint.vala:
private bool report_tls_warnings(string cx_type, TlsCertificateFlags warnings) {
// TODO: Report or verify flags with user, but for now merely
log for informational/debugging
// reasons and accede
message("%s TLS warnings connecting to %s: %Xh (%s)", cx_type,
to_string(), warnings, tls_flags_to_string(warnings));
return true;
}
It turns out that this is not an issue unknown to the developers, there is an open ticket that goes as far back as 2012. Our report prompted them to prioritize a fix. Big thank you to Geary developer Jim Nelson for acknowledging that this is a serious vulnerability for Geary users, some of whom are exposed to a high risk of active network interference.